- Incident Response Analysts are critical in detecting, investigating, and responding to cyber threats, ensuring business continuity after attacks.
- Essential skills needed in this role include threat detection & analysis, scripting & automation, problem-solving, and the ability to work under pressure and collaborate with teams.
- The career offers strong job security due to the growing demand for cybersecurity professionals and the shortage of qualified candidates.
Picture this: a cyberattack hits, and systems are compromised – who do you call? That’s where Incident Response Analysts come in! They’re the cybersecurity heroes who jump into action, quickly identifying and neutralizing threats to keep organizations safe.
Incident response is like firefighting in the digital world, tackling everything from malware to data breaches. In this blog, we’ll explain what an Incident Response Analyst does, how to become one, and why this role is more crucial than ever.
What Is an Incident Response Analyst?
An Incident Response Analyst is a cybersecurity professional who helps detect, investigate, and respond to security threats. Their main job is to protect an organization’s computer systems from cyberattacks, data breaches, and other security issues.
When a security incident happens, they analyze the situation, find out what caused it, and take steps to fix the problem and prevent future attacks.
These analysts usually work in a Security Operations Center (SOC) or as part of an organization’s cybersecurity team. They may be employed by large companies, government agencies, financial institutions, or cybersecurity firms. Their work involves:
- Monitoring security alerts
- Conducting digital forensics
- Creating reports on security incidents
- Helping improve security policies
- Training employees on how to avoid cyber threats
These specialists are the backbone of any business, ensuring that businesses can continue running without major disruptions from cyber threats.
Key Responsibilities of an Incident Response Analyst
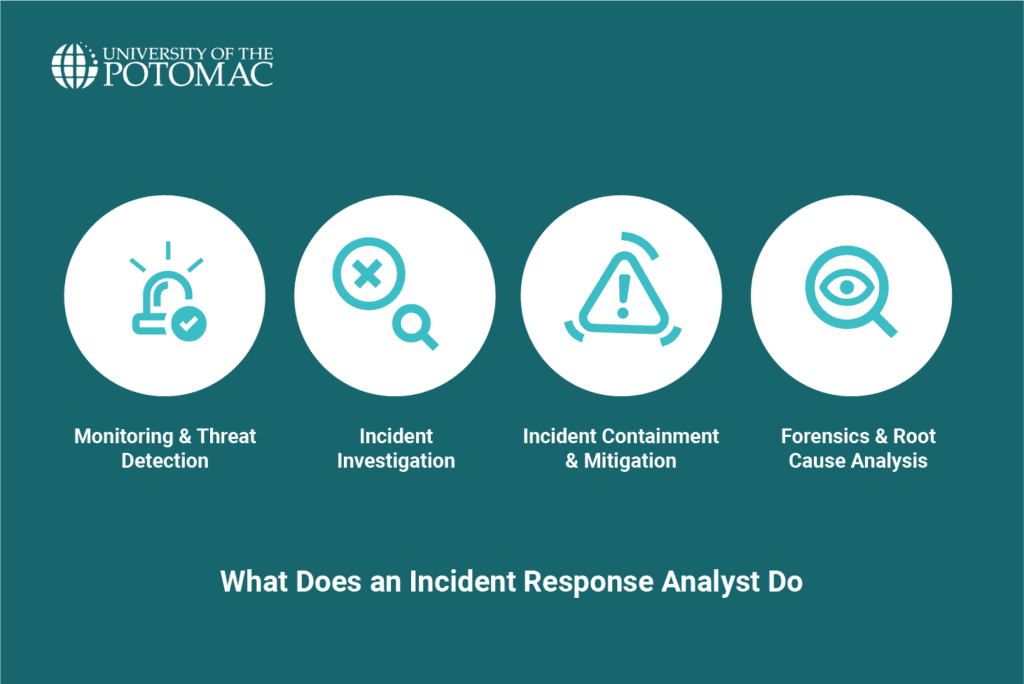
To keep businesses safe from cyberattacks, Incident Response Analysts are responsible for monitoring and detecting threats, investigating incidents when they occur, containing the threat, and finally, performing a thorough background check to identify the root cause of a specific incident.
Monitoring & threat detection
Incident Response Analysts keep an eye on networks, computers, and cloud systems to spot anything suspicious. They use SIEM (Security Information and Event Management) tools, Intrusion Detection Systems (IDS), and firewalls to track and analyze security events in real time. These tools help them quickly detect threats before they cause serious damage.
Analysts look for signs of:
- Phishing attacks, where hackers trick people into giving away passwords.
- They also watch for malware infections, which can harm systems or steal data.
- Unauthorized access attempts are another major concern, as attackers may try to break into networks. Insider threats, where employees misuse access, are also monitored.
- Lastly, analysts defend against DDoS (Distributed Denial of Service) attacks, which can crash websites by overwhelming them with fake traffic.
By constantly monitoring for these threats, Incident Response Analysts help keep businesses safe and stop cyberattacks before they become major problems.
Incident investigation
When an Incident Response Analyst detects a possible security threat, they begin investigating to understand what happened. First, they analyze logs, alerts, and system activity to gather clues about the incident. They check where the threat came from, how it spread, and what systems it affected.
Next, they verify if the threat is real or just a false alarm. Cybersecurity tools sometimes trigger alerts that turn out to be harmless, so analysts carefully review data to confirm whether action is needed.
Once they confirm the incident, they determine its impact. They assess if sensitive data was stolen, hackers gained control of a system, or the attack disrupted operations. This step helps organizations understand how serious the problem is and what needs to be fixed.
When carefully investigating security incidents, analysts help contain threats quickly, prevent further damage, and strengthen security to stop future attacks.
Incident containment & mitigation
Once a security threat has been confirmed, these experts take immediate action to contain and neutralize it before it spreads. The first step is isolating affected systems to prevent further damage. This may involve disconnecting compromised devices from the network, blocking malicious IP addresses, or disabling user accounts involved in the attack.
Next, they work to remove the threat from the system. If malware is detected, they use antivirus tools or specialized software to eliminate it. For unauthorized access, they reset passwords, revoke suspicious permissions, and strengthen security controls.
After neutralizing the threat, they ensure business continuity by restoring affected systems from secure backups and verifying that operations can resume safely. They also patch vulnerabilities and apply security updates to prevent the same attack from happening again.
Throughout the process, analysts document their actions and communicate with IT teams, management, and legal departments if needed. Their quick and effective response helps organizations recover from cyberattacks while minimizing downtime and data loss.
Forensics & root cause analysis
After containing a security threat, an Incident Response Analyst digs deeper to understand its root cause – how the attack happened and how to prevent it from happening again. They analyze system logs, network traffic, and security alerts to trace the attack’s origin and uncover vulnerabilities that were exploited.
Using digital forensics tools, they examine compromised files, malicious code, and system activity to determine how the attacker gained access. They may also review employee actions, software configurations, or security gaps that contributed to the breach.
Once they identify the cause, they work with IT and security teams to close security gaps. This could involve patching software, improving firewall rules, updating security policies, or strengthening user authentication.
The analyst also documents findings in a report, explaining how the attack occurred and recommending security improvements. These insights help organizations refine their defenses, train employees on cybersecurity best practices, and adjust monitoring systems to detect similar threats in the future.
How to Become an Incident Response Analyst
Becoming an Incident Response Analyst requires a mix of cybersecurity knowledge, technical skills, and hands-on experience. Whether you’re starting from an IT role or studying cybersecurity, the right education, training, and certifications can help you land a job in this critical and fast-growing career.
Education requirements
Most Incident Response Analysts have a bachelor’s degree in cybersecurity, computer science, or information technology. These degrees provide a strong foundation in network security, system administration, and threat detection. Some employers may accept degrees in related fields like engineering or mathematics, especially if combined with relevant experience.
For those without a degree, alternative education paths include cybersecurity boot camps, online courses, and industry certifications. Many professionals enter the field through hands-on training, self-study, or transitioning from IT roles like system administration or network security.
Key knowledge areas include operating systems, networking, cryptography, digital forensics, and ethical hacking. Understanding how cyberattacks work and how to defend against them is essential.
Regardless of the path taken, building practical skills through labs, simulations, or internships can improve job prospects.
Certifications
Certifications help Incident Response Analysts stand out in the cybersecurity job market by proving their skills and expertise. Some of the most valuable certifications include:
- GIAC Certified Incident Handler (GCIH) – Focuses on detecting, responding to, and recovering from cyber threats. It’s great for learning real-world attack techniques and defense strategies.
- Certified Information Systems Security Professional (CISSP) – A high-level certification covering security policies, risk management, and incident response. It’s best for those looking to advance into senior roles.
- Certified Ethical Hacker (CEH) – Teaches ethical hacking techniques to help professionals think like attackers. This knowledge helps analysts spot vulnerabilities and improve security defenses.
These certifications prove technical expertise and give job seekers an edge in a competitive field. Many employers prefer or even require them, making them a great investment for anyone looking to grow in cybersecurity.
Interested in pursuing a degree?
Fill out the form and get all admission information you need regarding your chosen program.
This will only take a moment.
Message Received!
Thank you for reaching out to us. We will review your message and get right back to you within 24 hours.
If there is an urgent matter and you need to speak to someone immediately you can call at the following phone number:
- We value your privacy.
Essential Skills
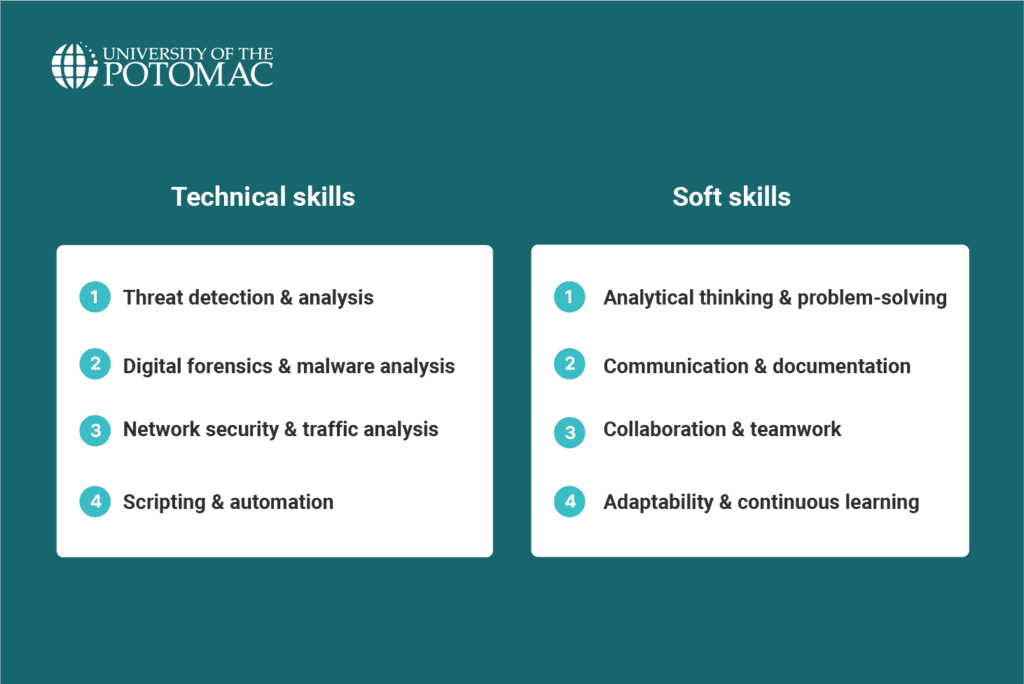
To become a successful Incident Response Analyst, you need a combination of technical cybersecurity skills and soft, interpersonal skills. The technical skills help you tackle the complex problems in cybersecurity, while soft skills enable you to communicate effectively and work well with others.
Technical skills
- Threat detection & analysis: Identifying unusual activity in systems and networks using security tools like SIEM and IDS. Analysts need to know how to spot potential threats early.
- Digital forensics & malware analysis: Investigating compromised systems, analyzing malware, and finding traces of how an attack occurred. It requires knowledge of file systems and forensic tools.
- Network security & traffic analysis: Understanding how to protect networks and analyze traffic to detect and prevent attacks. Familiarity with firewalls, VPNs, and network protocols is essential.
- Scripting & automation: Using programming languages like Python or Bash to automate tasks, improve efficiency, and streamline threat detection processes.
Soft skills
- Analytical thinking & problem-solving: The ability to think critically and piece together information to solve complex problems quickly.
- Communication & documentation: Clear reporting of incidents and findings, as well as explaining technical issues to non-technical stakeholders.
- Collaboration & teamwork: Working closely with IT, management, and other security professionals to address incidents and improve security measures.
- Adaptability & continuous learning: The cybersecurity landscape changes constantly. Analysts must stay updated on new threats and tools to remain effective.
Career Outlook and Salary Expectations
Incident Response Analysts are in high demand due to the escalating frequency and sophistication of cyber threats, including ransomware attacks and data breaches.
The global shortage of cybersecurity professionals exacerbates this issue, making it challenging for organizations to find qualified experts. According to a 2022 report, there is a global shortage of 3.4 million cybersecurity professionals, with 663,434 job openings in the U.S. alone.
This talent gap has significant implications for organizations’ security postures. Another 2023 report from the World Economic Forum highlights that by 2030, the global talent shortage could exceed 85 million workers, potentially leading to an estimated $8.5 trillion in unrealized annual revenue.
In terms of compensation, the average salary for an Incident Response Analyst varies based on experience and location. That being said, the national average hourly wage is approximately $46.45, equating to an annual salary of about $96,500.
However, this figure can vary; for instance, in Chicago, Illinois, the average base salary ranges from $74,000 to $93,000, with a total cash compensation averaging $86,500.
These figures highlight the critical need for skilled Incident Response Analysts and the cybersecurity career benefits, including competitive compensation, offered to attract and retain talent in this vital field.
Conclusion
Cybersecurity is a rapidly-growing field, with a huge demand for Incident Response Analysts to protect organizations from rising threats like ransomware and data breaches.
The shortage of skilled professionals makes this career path even more exciting and rewarding than ever. If you’re passionate about solving problems and staying ahead of cybercriminals, this could be the perfect field for you.
If you’re seeking to get started in cybersecurity, enroll in the Cybersecurity BA program at Potomac today and gain the skills needed to make a real difference in this critical industry.
Frequently Asked Questions (FAQs):
What is the difference between an Incident Response Analyst and a SOC Analyst?
An Incident Response Analyst focuses on investigating, containing, and recovering from cybersecurity incidents, while a SOC analyst monitors security events in real time, detects potential threats, and escalates incidents to the response team.
What are the biggest challenges in incident response?
The biggest challenges in incident response include identifying and mitigating advanced threats quickly, coordinating between teams, and ensuring minimal downtime while maintaining thorough documentation and preventing future attacks.










